Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
- Weiler810T
-
 Topic Author
Topic Author
- Visitor
-

07 Dec 2019 10:36 - 07 Dec 2019 10:46 #152227
by Weiler810T
Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios was created by Weiler810T
Hello
I'm playing around with Mint 19.3 and want to install Linuxcnc. It fails because of a signed RT kernel.
Compile running but not signed for UEFI-bios.
Any ideas?
Howto for signed RT-Kernel?
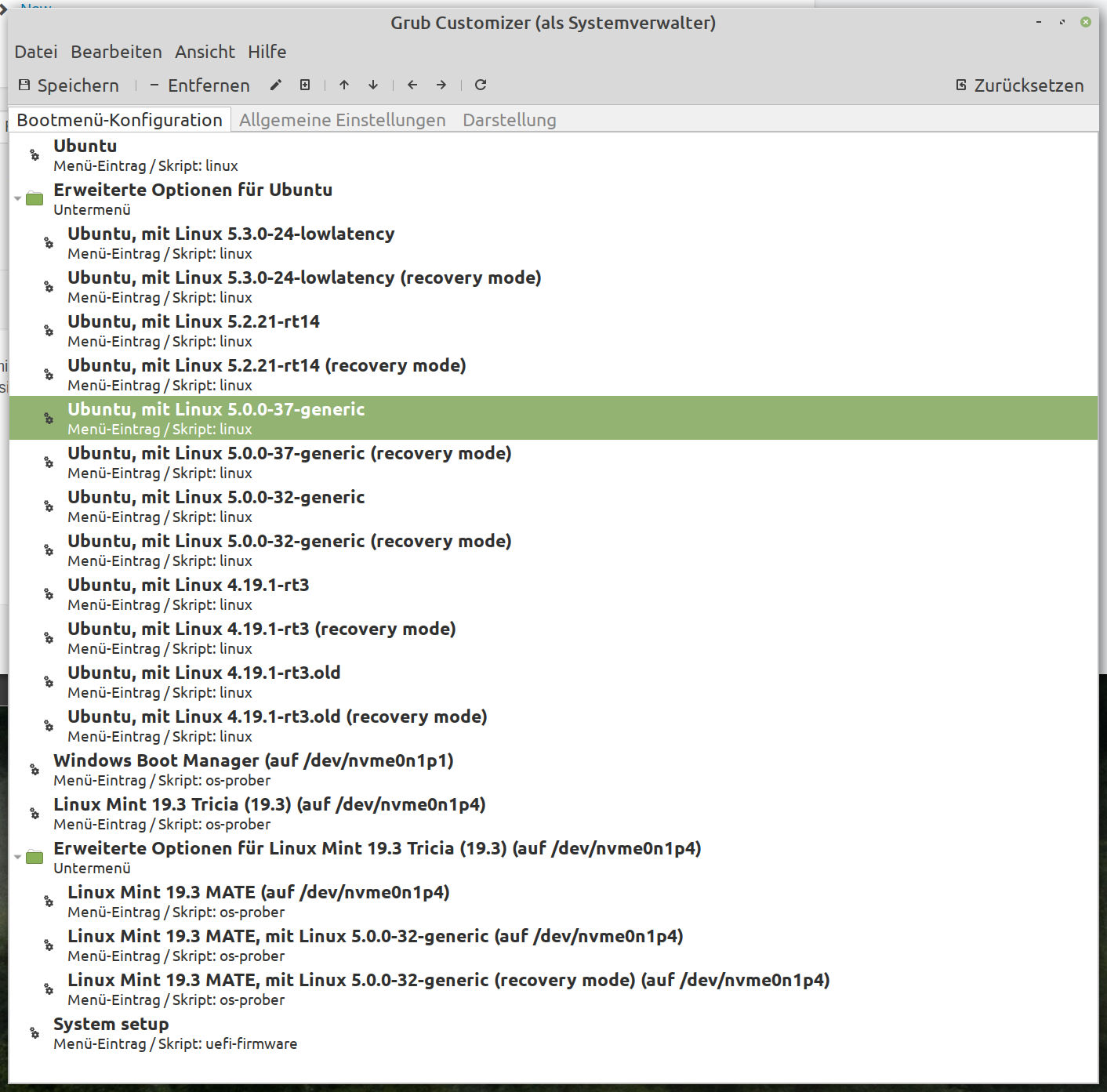
Bootmenue
Hardware
I'm playing around with Mint 19.3 and want to install Linuxcnc. It fails because of a signed RT kernel.
Compile running but not signed for UEFI-bios.
Any ideas?
Howto for signed RT-Kernel?
Bootmenue
Hardware
chiron@chiron-SystemFZ16:~$ halcompile
halcompile: Befehl nicht gefunden.
chiron@chiron-SystemFZ16:~$ inxi -Fz
System:
Host: chiron-SystemFZ16 Kernel: 5.3.0-24-lowlatency x86_64 bits: 64
Desktop: MATE 1.22.2 Distro: Linux Mint 19.3 Tricia
Machine:
Type: Desktop Mobo: ASUSTeK model: TUF Z390-PRO GAMING v: Rev X.0x
serial: <filter> UEFI: American Megatrends v: 2417 date: 06/03/2019
CPU:
Topology: 8-Core model: Intel Core i7-9700KF bits: 64 type: MCP
L2 cache: 12.0 MiB
Speed: 801 MHz min/max: 800/5100 MHz Core speeds (MHz): 1: 800 2: 800
3: 800 4: 800 5: 800 6: 800 7: 800 8: 800
Graphics:
Device-1: NVIDIA GP107GL [Quadro P1000] driver: nouveau v: kernel
Display: x11 server: X.Org 1.20.4 driver: modesetting unloaded: fbdev,vesa
resolution: 3840x2160~60Hz
OpenGL: renderer: NV137 v: 4.3 Mesa 19.0.8
Audio:
Device-1: Intel Cannon Lake PCH cAVS driver: snd_hda_intel
Device-2: NVIDIA GP107GL High Definition Audio driver: snd_hda_intel
Sound Server: ALSA v: k5.3.0-24-lowlatency
Network:
Device-1: Intel Ethernet I219-V driver: e1000e
IF: eno1 state: up speed: 100 Mbps duplex: full mac: <filter>
Drives:
Local Storage: total: 2.73 TiB used: 91.98 GiB (3.3%)
ID-1: /dev/nvme0n1 vendor: Samsung model: SSD 970 EVO Plus 500GB
size: 465.76 GiB
ID-2: /dev/sda vendor: Samsung model: SSD 860 EVO 500GB size: 465.76 GiB
ID-3: /dev/sdb type: USB vendor: Seagate model: ST2000LM007-1R8174
size: 1.82 TiB
Partition:
ID-1: / size: 456.96 GiB used: 62.74 GiB (13.7%) fs: ext4 dev: /dev/sda2
Sensors:
System Temperatures: cpu: 37.0 C mobo: N/A gpu: nouveau temp: 41 C
Fan Speeds (RPM): cpu: 0 gpu: nouveau fan: 1721
Info:
Processes: 268 Uptime: 25m Memory: 31.28 GiB used: 1.29 GiB (4.1%)
Shell: bash inxi: 3.0.32
chiron@chiron-SystemFZ16:~$
Last edit: 07 Dec 2019 10:46 by Weiler810T.
Please Log in or Create an account to join the conversation.
- tommylight
-

- Away
- Moderator
-

Less
More
- Posts: 21185
- Thank you received: 7239
07 Dec 2019 11:36 #152232
by tommylight
Replied by tommylight on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
Please Log in or Create an account to join the conversation.
- Weiler810T
-
 Topic Author
Topic Author
- Visitor
-

07 Dec 2019 13:07 #152242
by Weiler810T
Replied by Weiler810T on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
Attachments:
Please Log in or Create an account to join the conversation.
- PCW
-

- Offline
- Moderator
-

Less
More
- Posts: 17605
- Thank you received: 5148
07 Dec 2019 14:51 #152254
by PCW
Replied by PCW on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
Can you disable secure boot in your BIOS?
Please Log in or Create an account to join the conversation.
- Weiler810T
-
 Topic Author
Topic Author
- Visitor
-

07 Dec 2019 14:56 #152256
by Weiler810T
Replied by Weiler810T on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
No, you can sign the kernel yourself, no idea how it works with sbsign, you have to make me smart first 
chiron@chiron-SystemFZ16:~$ sbsign
Usage: sbsign [options] --key <keyfile> --cert <certfile> <efi-boot-image>
Sign an EFI boot image for use with secure boot.
Options:
--key <keyfile> signing key (PEM-encoded RSA private key)
--cert <certfile> certificate (x509 certificate)
--detached write a detached signature, instead of
a signed binary
--output <file> write signed data to <file>
(default <efi-boot-image>.signed,
or <efi-boot-image>.pk7 for detached
signatures)
chiron@chiron-SystemFZ16:~$ sudo update-secureboot-policy --enroll-key
[sudo] Passwort für chiron:
Das hat nicht funktioniert, bitte nochmal probieren.
[sudo] Passwort für chiron:
No DKMS modules installed.
chiron@chiron-SystemFZ16:~$ kmodsign sha512 \
> /var/lib/shim-signed/mok/MOK.priv \
> /var/lib/shim-signed/mok/MOK.der \
> module.ko
At main.c:248:
- SSL error:0200100D:system library:fopen:Permission denied: ../crypto/bio/bss_file.c:72
- SSL error:2006D002:BIO routines:BIO_new_file:system lib: ../crypto/bio/bss_file.c:81
kmodsign: /var/lib/shim-signed/mok/MOK.priv: Permission denied
chiron@chiron-SystemFZ16:~$ bootctl status
System:
Firmware: n/a (n/a)
Secure Boot: enabled
Setup Mode: user
Current Loader:
Product: n/a
ESP: n/a
File: └─n/a
Boot Loader Entries in EFI Variables:
Title: ubuntu
ID: 0x0000
Status: active, boot-order
Partition: /dev/disk/by-partuuid/78c218fe-ad21-4d06-8f51-49f60788bce8
File: └─/EFI/UBUNTU/SHIMX64.EFI
Title: Windows Boot Manager
ID: 0x0001
Status: active, boot-order
Partition: /dev/disk/by-partuuid/59227b98-689c-4ffd-93c0-cba35beb987f
File: └─/EFI/MICROSOFT/BOOT/BOOTMGFW.EFI
Title: debian
ID: 0x0005
Status: active, boot-order
Partition: /dev/disk/by-partuuid/78c218fe-ad21-4d06-8f51-49f60788bce8
File: └─/EFI/DEBIAN/GRUBX64.EFI
Title: ubuntu
ID: 0x0009
Status: active, boot-order
Partition: /dev/disk/by-partuuid/59227b98-689c-4ffd-93c0-cba35beb987f
File: └─/EFI/UBUNTU/SHIMX64.EFI
chiron@chiron-SystemFZ16:~$ mok-util
Der Befehl 'mok-util' wurde nicht gefunden, meinten Sie:
Befehl 'mokutil' aus dem deb mokutil
Versuche: sudo apt install <deb name>
chiron@chiron-SystemFZ16:~$ sudo apt install mokutil
[sudo] Passwort für chiron:
Paketlisten werden gelesen... Fertig
Abhängigkeitsbaum wird aufgebaut.
Statusinformationen werden eingelesen.... Fertig
mokutil ist schon die neueste Version (0.3.0+1538710437.fb6250f-0ubuntu2~18.04.1).
Die folgenden Pakete wurden automatisch installiert und werden nicht mehr benötigt:
libgladeui-2-6 libgladeui-common
Verwenden Sie »sudo apt autoremove«, um sie zu entfernen.
0 aktualisiert, 0 neu installiert, 0 zu entfernen und 0 nicht aktualisiert.
chiron@chiron-SystemFZ16:~$ sudo apt autoremove
Paketlisten werden gelesen... Fertig
Abhängigkeitsbaum wird aufgebaut.
Statusinformationen werden eingelesen.... Fertig
Die folgenden Pakete werden ENTFERNT:
libgladeui-2-6 libgladeui-common
0 aktualisiert, 0 neu installiert, 2 zu entfernen und 0 nicht aktualisiert.
Nach dieser Operation werden 8.936 kB Plattenplatz freigegeben.
Möchten Sie fortfahren? [J/n] j
(Lese Datenbank ... 507063 Dateien und Verzeichnisse sind derzeit installiert.)
Entfernen von libgladeui-2-6:amd64 (3.22.1-1) ...
Entfernen von libgladeui-common (3.22.1-1) ...
Trigger für libc-bin (2.27-3ubuntu1) werden verarbeitet ...
chiron@chiron-SystemFZ16:~$ mokutil
Usage:
mokutil OPTIONS [ARGS...]
Options:
--help Show help
--list-enrolled List the enrolled keys
--list-new List the keys to be enrolled
--list-delete List the keys to be deleted
--import <der file...> Import keys
--delete <der file...> Delete specific keys
--revoke-import Revoke the import request
--revoke-delete Revoke the delete request
--export Export keys to files
--password Set MOK password
--clear-password Clear MOK password
--disable-validation Disable signature validation
--enable-validation Enable signature validation
--sb-state Show SecureBoot State
--test-key <der file> Test if the key is enrolled or not
--reset Reset MOK list
--generate-hash[=password] Generate the password hash
--ignore-db Ignore DB for validation
--use-db Use DB for validation
--import-hash <hash> Import a hash into MOK or MOKX
--delete-hash <hash> Delete a hash in MOK or MOKX
--set-verbosity <true/false> Set the verbosity bit for shim
--pk List the keys in PK
--kek List the keys in KEK
--db List the keys in db
--dbx List the keys in dbx
--timeout <-1,0..0x7fff> Set the timeout for MOK prompt
Supplimentary Options:
--hash-file <hash file> Use the specific password hash
--root-pw Use the root password
--simple-hash Use the old password hash method
--mokx Manipulate the MOK blacklist
chiron@chiron-SystemFZ16:~$ mokutil --pk
[key 1]
SHA1 Fingerprint: ec:d9:88:46:2e:bc:25:e7:ee:a7:91:72:08:9e:f3:fd:d1:b0:24:97
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
53:41:e0:15:c4:3a:f8:a8:48:36:b9:a5:ff:69:14:88
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=ASUSTeK MotherBoard PK Certificate
Validity
Not Before: Dec 26 23:34:50 2011 GMT
Not After : Dec 26 23:34:49 2031 GMT
Subject: CN=ASUSTeK MotherBoard PK Certificate
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:d9:84:15:36:c5:d4:ce:8a:a1:56:16:a0:e8:74:
cd:58:1e:2a:02:96:1b:c4:37:64:da:8c:6a:24:84:
cd:dc:c4:68:04:15:c7:e9:cf:20:a4:45:1a:42:f0:
a3:9b:62:22:6e:2a:43:67:17:8d:4d:10:aa:f8:dd:
f2:2a:9e:86:ba:91:d0:32:7e:95:be:01:78:73:3a:
d3:98:7e:19:f8:16:0e:27:cc:ea:c5:be:b5:80:7e:
e8:bc:a8:17:41:b3:ea:55:34:19:53:d7:7e:7d:50:
c7:5a:b8:ef:54:f9:13:6e:ab:d6:45:cd:1d:02:94:
e2:78:d7:88:a8:10:52:8d:7e:ba:f1:49:36:c0:68:
70:f9:d5:0c:5a:fd:6b:1a:6f:88:c2:37:69:22:42:
92:f3:9d:ae:ef:73:ec:f4:0f:32:42:64:c3:e9:b9:
89:dd:06:e5:cc:2f:6b:f8:00:4e:91:64:f7:03:45:
f0:4f:a4:11:83:e9:83:97:e9:a0:dc:2d:c8:03:56:
b4:df:61:a6:32:a5:8b:a6:1b:4e:d8:1c:a7:a3:f3:
72:4e:72:f8:fe:69:49:cf:61:f2:e6:59:96:58:b8:
14:7c:ca:f5:e5:6b:f0:6d:da:f7:bc:08:5b:7f:57:
e9:96:37:59:5a:70:79:57:0e:c8:82:c8:91:7b:67:
f9:2d
Exponent: 65537 (0x10001)
X509v3 extensions:
2.5.29.1:
?=.../0-1+0)..U..."ASUSTeK MotherBoard PK Certificate..SA...:..H6...i..
Signature Algorithm: sha256WithRSAEncryption
73:27:1a:32:88:0e:db:13:8d:f5:7e:fc:94:f2:1a:27:6b:c2:
ca:79:d0:ba:b6:58:bc:df:97:13:5a:4c:dc:a2:e4:90:39:7b:
24:84:7d:2e:a3:95:96:39:a6:6b:c2:a6:51:38:6f:e5:0b:af:
c0:91:0a:90:3f:3e:5a:e4:79:16:98:96:32:94:49:ae:00:28:
18:aa:ef:fb:54:95:93:c7:fc:e4:89:ef:96:00:ce:d6:c6:8a:
4d:85:ca:9c:6c:fb:8a:a7:43:60:36:5e:73:97:17:2f:16:46:
d0:ce:f0:a0:07:77:62:4d:15:0e:22:f6:91:71:1a:79:e1:85:
1c:0b:2c:94:9f:9d:97:cf:49:b5:dd:ea:6a:e5:a7:61:ec:82:
0d:95:e8:98:5c:e8:72:c6:da:8d:df:21:ec:05:30:0f:79:b8:
af:e9:b0:2b:c0:83:73:fe:bf:9d:4a:6d:da:a5:a0:65:37:cf:
2c:87:f1:2b:c6:a3:0e:92:64:57:1a:77:ed:d9:47:40:47:da:
ea:ff:23:98:d1:25:b9:72:f5:38:3a:b3:33:a5:5d:f1:44:dc:
d8:63:7d:f9:2f:7d:f1:d1:d0:95:c0:a6:75:a8:70:c9:c4:2b:
c0:45:04:d0:40:5b:75:7d:e2:b2:0a:3c:1e:64:22:30:d2:02:
84:c5:b7:bb
chiron@chiron-SystemFZ16:~$ sbsign
Usage: sbsign [options] --key <keyfile> --cert <certfile> <efi-boot-image>
Sign an EFI boot image for use with secure boot.
Options:
--key <keyfile> signing key (PEM-encoded RSA private key)
--cert <certfile> certificate (x509 certificate)
--detached write a detached signature, instead of
a signed binary
--output <file> write signed data to <file>
(default <efi-boot-image>.signed,
or <efi-boot-image>.pk7 for detached
signatures)
chiron@chiron-SystemFZ16:~$ Please Log in or Create an account to join the conversation.
- PCW
-

- Offline
- Moderator
-

Less
More
- Posts: 17605
- Thank you received: 5148
07 Dec 2019 15:01 - 07 Dec 2019 15:01 #152257
by PCW
Replied by PCW on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
Seems like a lot of trouble (and something would have to be redone every time you updated a kernel module)
If It were my choice I would recycle any PC that doesn't allow you to disable secure boot
If It were my choice I would recycle any PC that doesn't allow you to disable secure boot
Last edit: 07 Dec 2019 15:01 by PCW.
Please Log in or Create an account to join the conversation.
- Weiler810T
-
 Topic Author
Topic Author
- Visitor
-

07 Dec 2019 15:52 #152263
by Weiler810T



Replied by Weiler810T on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
If It were my choice I would recycle any PC that doesn't allow you to disable secure boot
Please Log in or Create an account to join the conversation.
- tommylight
-

- Away
- Moderator
-

Less
More
- Posts: 21185
- Thank you received: 7239
07 Dec 2019 20:29 #152284
by tommylight
And i agree with PCW, secure boot has nothing secure in it and UEFI is the biggest mistake in computer history. It was done solely for the purpose of enabling Microsoft and disabling everything else. Luckily it does not work as intended so we can continue to use Linux.
Replied by tommylight on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
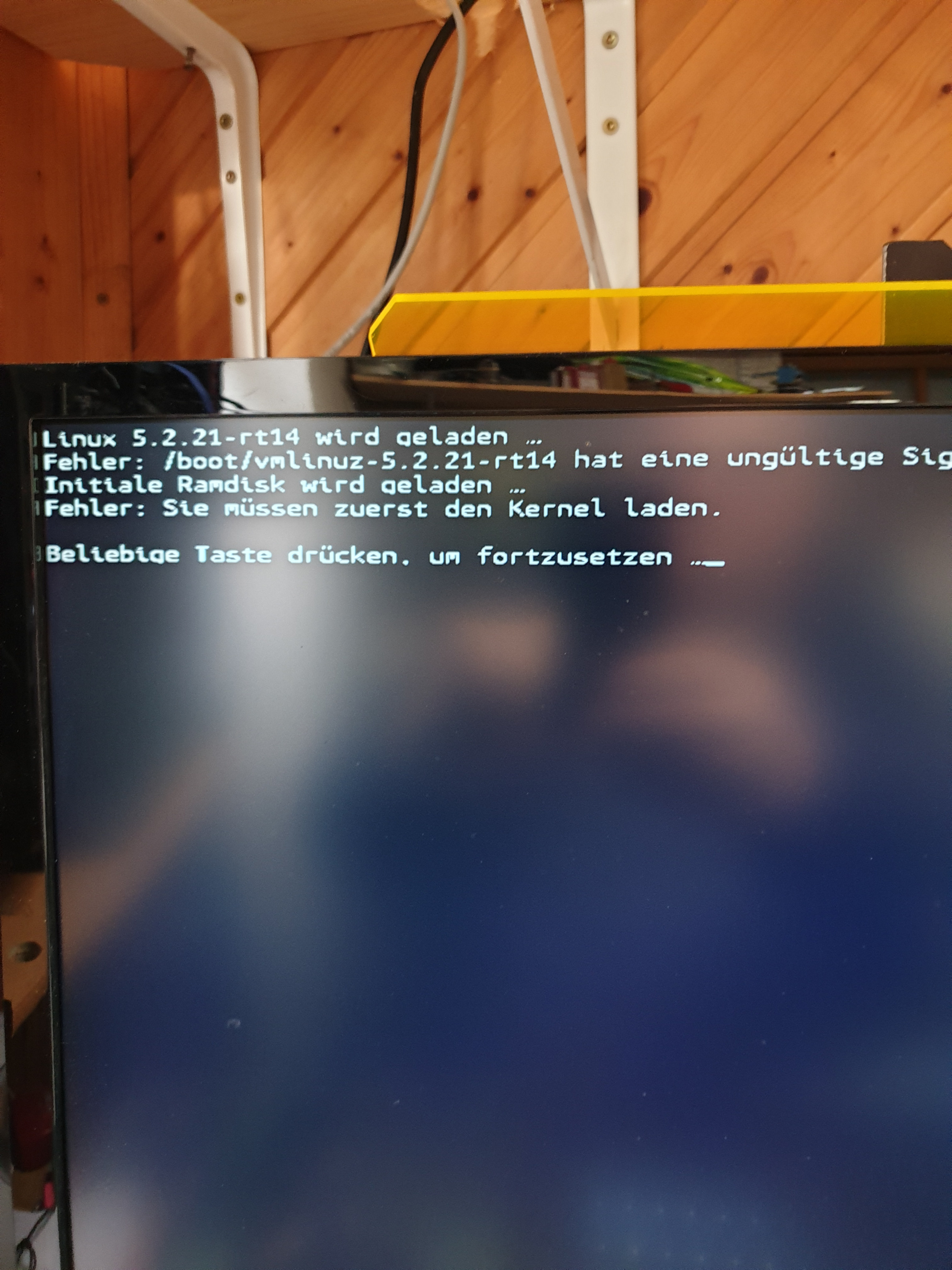
That is still 5.2....something kernel, did you try the one linked on the link i linked to ?hello Tommy
doesn't work, unsigned kernel
hmmm...
And i agree with PCW, secure boot has nothing secure in it and UEFI is the biggest mistake in computer history. It was done solely for the purpose of enabling Microsoft and disabling everything else. Luckily it does not work as intended so we can continue to use Linux.
Please Log in or Create an account to join the conversation.
- Weiler810T
-
 Topic Author
Topic Author
- Visitor
-

07 Dec 2019 21:05 #152290
by Weiler810T
Replied by Weiler810T on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
I see it the same way, but i need windos for cad and the image linked by you has the same proplem.
I can install all dependencies for linuxcnc, but the fucking unsigned kernel doesn't work.
I can install all dependencies for linuxcnc, but the fucking unsigned kernel doesn't work.
Please Log in or Create an account to join the conversation.
- tommylight
-

- Away
- Moderator
-

Less
More
- Posts: 21185
- Thank you received: 7239
07 Dec 2019 21:37 #152297
by tommylight
Replied by tommylight on topic Linux Mint 19.3 + Signed RT Kernel failed + UEFI-Bios
there is a link for an unsigned kernel there and it does work always, last i installed was 5 days ago.
Please Log in or Create an account to join the conversation.
Time to create page: 0.281 seconds